- info@clossfile.com
- 345 Cedar St #115, St Paul MN 55101
Cyber Back-Tracking Security
"Retribution" - If any of your information is ever stolen!
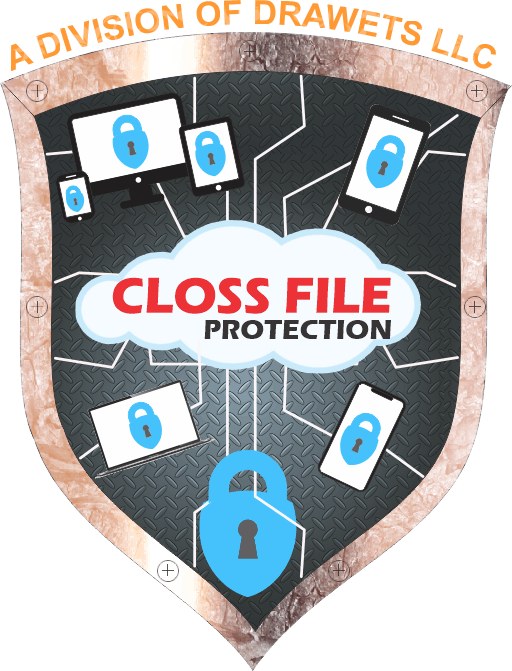
THE CLOSS FILES
If any of your data is ever taken – The CLOSS FILES will find it, once the thief puts your stolen information on their system, the CLOSS FILES will immediately, transmit the text messages, pictures and sms message, and if there is a camera on the illegal device it will take a picture of the thief, and upload all the information to a cloud drive – you will easily be able to find out who has taken your information!

Call Us
651 - 300 - 7755
"Retribution" CLOSS FILE PROTECTION - Discover who and where and what system(s) your stolen information is on!
99.9% SUCCESS RATE

Always Know The
Attacks Paths

Reduce Your
Hygiene Risk
Optimize Your Cyber
Resources

Make Data Driven
Decisions
We are Experts in
Data-Back-Tracking
Any information removed from your devices, without your permission will be taged with a CLOSS FILE, then all the information on the device your information was transferred to will be uploaded to the cloud server- from there it is a simple matter to find out who the crooks are.

Threat Intelligence + Response
Standard response if your data is stolen - THE CLOSS FILES - whatever device your information has been transferred to the CLOSS FILES will upload that devices information to the cloud servers.

Managed Enterpise Solutions
No matter the size of your organization, the CLOSS FILES, will collect the information needed for you to find out who has taken your information.
THE CLOSS FILES
Our Services

Network
Data Security
The CLOSS FILE will track any information taken from you landline network!

Wireless Network
Data Security
The CLOSS FILE will track any information taken from you wireless network

Web Application
Data Security
The CLOSS FILE will track any applications removed from your system!

Mobile Application
Data Security
The CLOSS FILES will track any information taken from you mobile devices!

Optimize Your Cyber
Data Security
The CLOSS FILES will track any information taken from you mobile devices!

Cyber Attack
Data Security
The CLOSS FILES will track any information taken from you any of your devices!

SmartScan Managed
Data Security
The CLOSS FILES will track any information taken from you mobile devices! and upload it to a cloud drive!
PCI Vulnerability
Data Security
No matter the method they use to steal your information – The CLOSS FILES will track your information – then upload all the text messages and pictures of any device your stolen information is placed on!